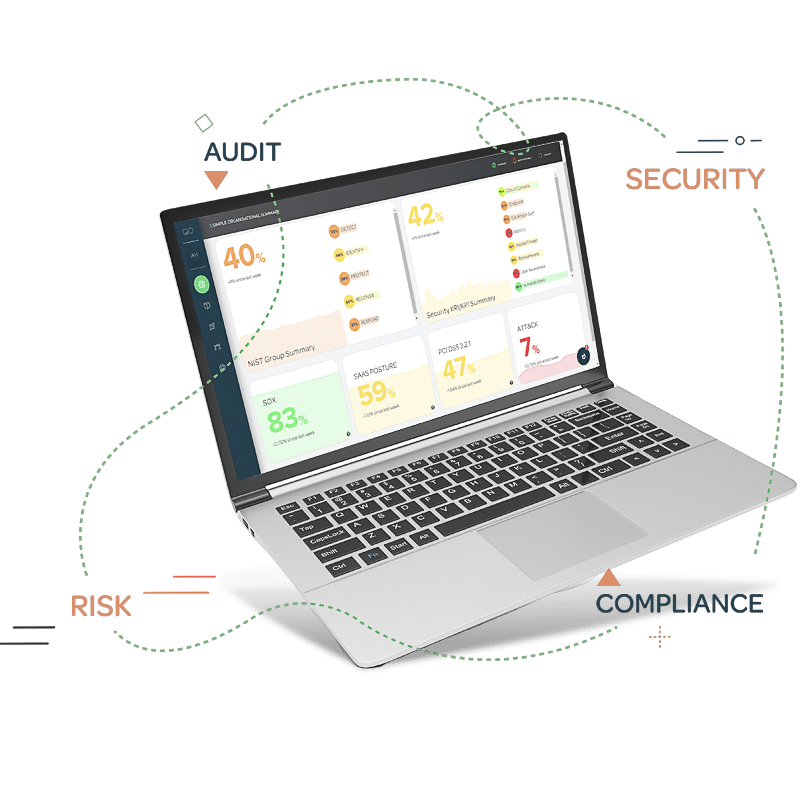
Cyber Asset Attack Surface Management and Asset Visibility
Understand your cyber attack surface with a complete asset inventory.
Secure your organisation with CAASM. Get continuous asset visibility and cyber asset attack surface management with our CAASM solution.
Asset Visibility is integral to operational resilience
Table of Contents
What is CAASM (Cyber Asset Attack Surface Management)?
Cyber Asset Attack Surface Management (CAASM) is a relatively new, emerging technology that identifies, monitors and manages the potential points of entry or vulnerability within an organisations digital infrastructure that could be exploited by cyber attackers. The “attack surface” refers to all the entry points, interfaces, systems, and components that can potentially be targeted by malicious actors.
As the attack surface is now evolving and increasing exponentially, coupled with rapid digital transformation, it has never been more imperative to fully understand your attack surface. However, this has become challenging in recent years, particularly for larger enterprises that have moved to the cloud and now have a mix of cloud, on-prem and potentially legacy tech and could be struggling to understand exactly what assets they have in their inventory to really comprehend what their potential attack surface is. Couple that with the progression in more flexible and hybrid working and BYOD has meant that it has become truly challenging for cyber security teams to fully be proactive in their cyber security architecture. Enterprises will remain vulnerable to attacks if they do not address the visibility they have of this limitless attack surface, because, frankly, keeping processes and policies the same, simply no longer cuts it.
Why do you need CAASM?
CAASM addresses this issue by supporting businesses in creating a live asset repository and a series of proactive measures to reduce an organisations attack surface and enhance its overall cybersecurity posture. Gartner further validates this with their latest Hype Cycle 2023 for Security Operations. By implementing a CAASM solution your organisation will ultimately significantly reduce its threat landscape because you will have a full understanding of assets, be able to review – in real time – your technology infrastructures risk levels and therefore be able to be considerably more proactive and reactive to cyber threats.

What are the benefits of CAASM?
Real-time, automated viewpoint of your Security Posture: Our CAASM solution helps organisations gain a clearer understanding of their digital attack surface, including all potential entry points that could be exploited by attackers. By identifying and addressing these vulnerabilities, organisations can significantly improve their overall security posture.
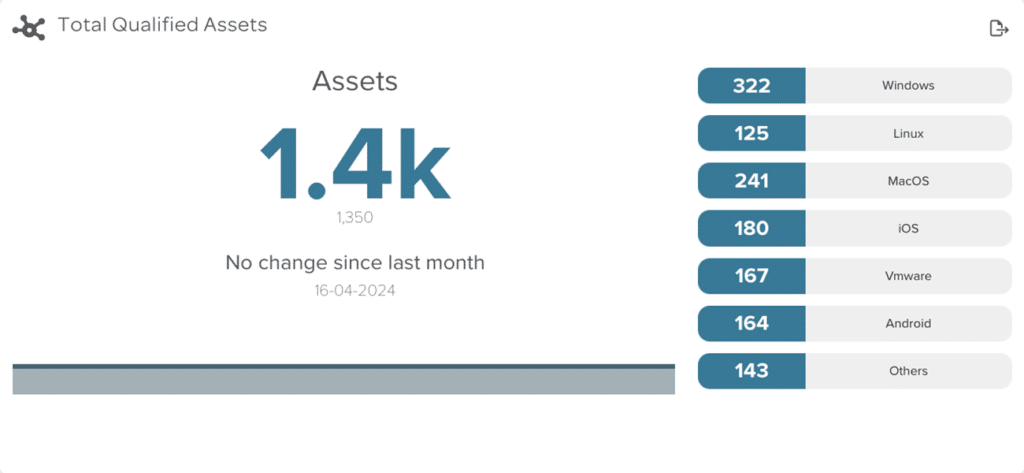
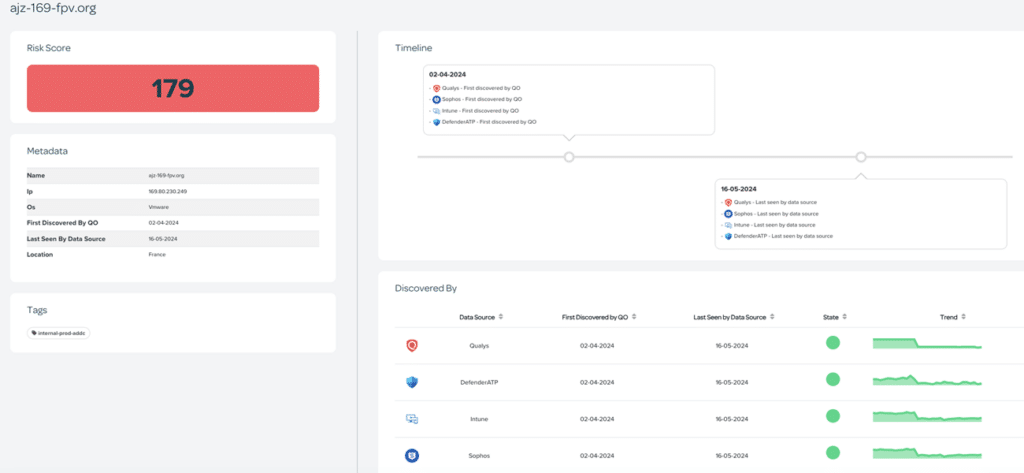
Risk Reduction: Identifying and mitigating vulnerabilities in the attack surface reduces the overall risk of a successful cyberattack. By proactively addressing weak points, organisations can minimise the potential impact of attacks and prevent data breaches.
Early Threat Detection: Continuous monitoring of the attack surface allows for early detection of potential threats and vulnerabilities. This enables security teams to respond swiftly to emerging risks and potential security breaches before they can be fully exploited.
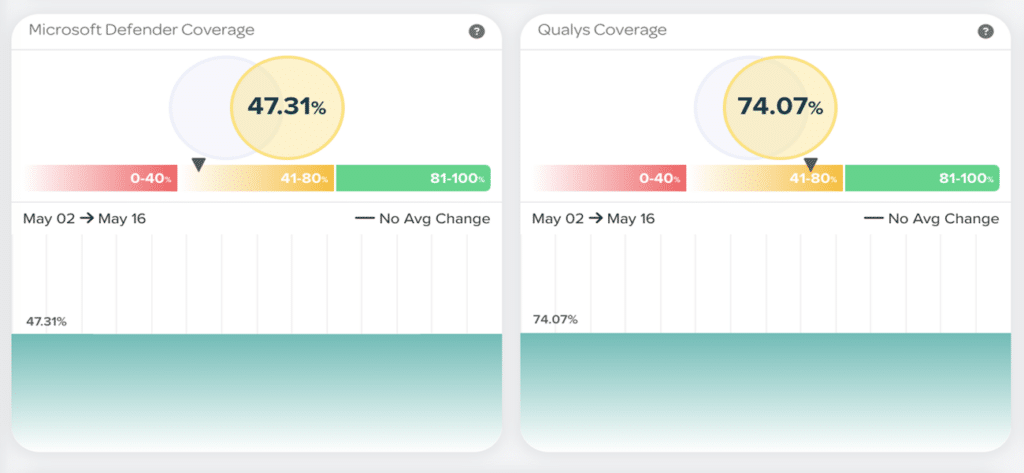
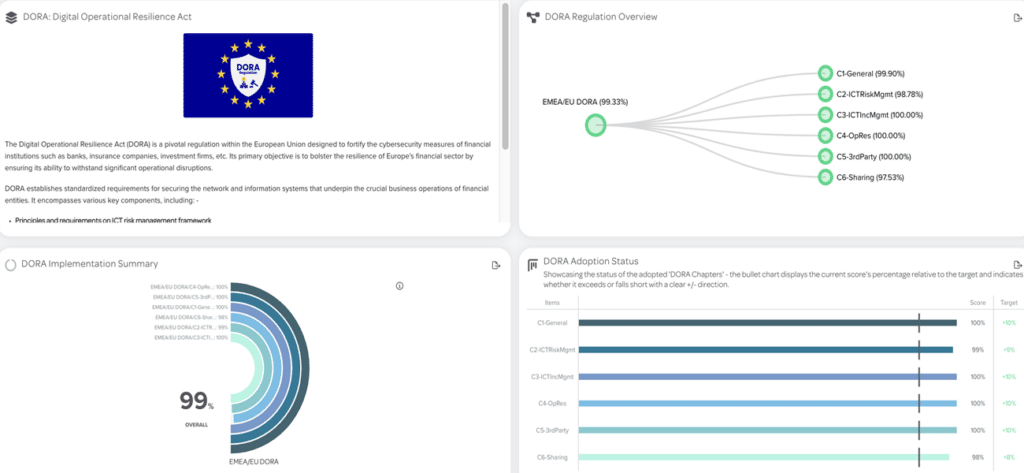
Regulatory Compliance: Many industries and regions have specific cybersecurity regulations and compliance requirements. CAASM can help organisations meet these requirements by actively managing their attack surface and ensuring that security controls are in place.

Reduced Attack Surface
Through continuous assessment and remediation, CAASM helps organisations reduce their attack surface by eliminating unnecessary or outdated assets, services or configurations that could be exploited by attackers.
Incident Response
In the event of a security incident, having a well-managed attack surface allows organisations to respond more effectively. Security teams can quickly identify the source of the breach and take appropriate actions to contain and mitigate the impact.

Third-Party Risk Management
Organisations often rely on third-party vendors and partners which can introduce additional vulnerabilities. CAASM helps in assessing and managing the risks associated with these external entities, ensuring that they adhere to proper security practices.

Strengthened Business Continuity
By proactively managing vulnerabilities and potential attack vectors, organisations can enhance their resilience and maintain business continuity, even in the face of cyber threats.
How is CAASM the start of the journey to CCM?
Depending on where an organisation is on their maturity journey, Cyber Asset Attack Surface Management can be the start of that journey to reach continuous controls monitoring and achieve the single source of truth into your entire organisations risk security and compliance posture.
CAASM is a critical component to the start of that maturity journey as it focuses on identifying and managing an organisation’s digital assets and their vulnerabilities.
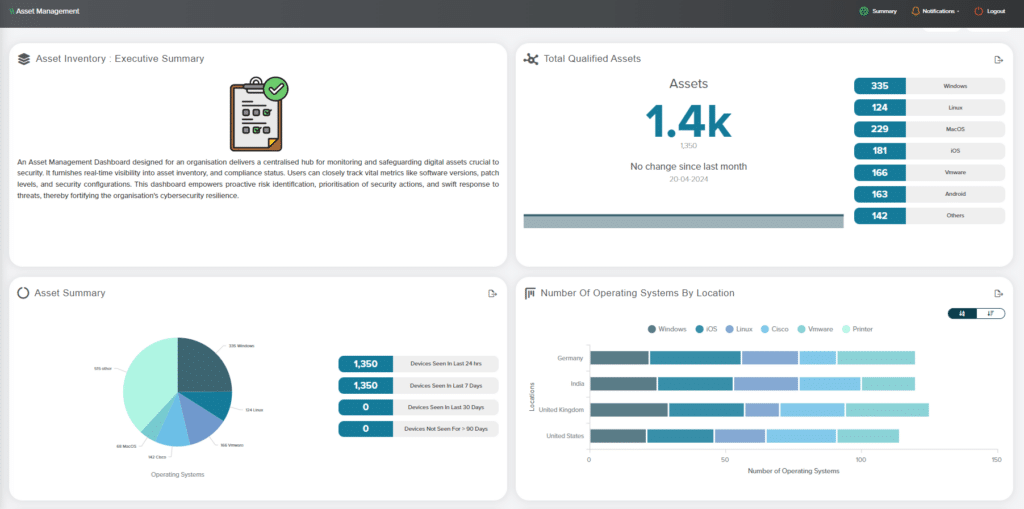
Once assets are discovered it creates an asset inventory which is the essential foundation for CCM – in order to monitor your controls effectively you need to understand exactly what you are protecting.
When an organisation has implemented cyber attack surface management they can then move on to gain an understanding of their vulnerabilities and cyber risks and then, ultimately, onto ensuring their regulatory compliance to their frameworks. At this point Continuous Controls monitoring can be achieved.
Find out more about CAASM
Who is CAASM for?
Cyber Asset Attack Surface Management is primarily for organisations concerned with protecting their digital assets, networks and systems from cyber threats and attacks. This could be larger enterprises and organisations that manage complex IT infrastructures or sensitive data and therefore need to ensure that their attack surface is monitored in real-time to prevent security breaches and protect that valuable data.
Cybersecurity professionals and IT teams who are responsible for implementing security measures and monitoring the attack surface (to ensure that vulnerabilities are identified and addressed promptly) are clearly the key stakeholders for CAASM, however the importance of cyber asset attack surface management extends to risk managers too. These are professionals that are responsible for managing and assessing risk within an organisation and can utilise the CAASM technology to make informed decisions about levels of risk within.
Compliance teams also benefit as they seek to understand their levels of compliance within a given framework. So by using CAASM technology they can monitor in real-time and, with the exclusion of manual processes, understand their compliance against a given regulatory framework.
Developers and DevOps Teams also benefit as they can understand vulnerabilities in the software development lifecycle and their role is integral in identifying and mitigating vulnerabilities before they make it into production.
Overall, Cyber Asset Attack Surface Management is essential for anyone who wants to safeguard their digital assets, maintain data privacy and prevent cyber threats from compromising their systems and information.
How do CAASM Solutions & Platforms work?
In order for organisations to remain ahead of the exponential rise in cyber risk threats, leveraging automation and minimising manual processes significantly has become key for cyber security professional to manage their attack surface.
The QO platform connects to any data source within your business (cloud, on-prem or legacy – digital and non-digital), so that your organisation can obtain a single source of truth to their attack surface – all in real-time and continuous – and that information is presented in a fully customised dashboard that helps you understand across all vectors which assets are most likely vulnerable from attack.
The CAASM Platform works by:
- Providing an accurate, live asset inventory
- Real time status of that inventory
- Continuously available
- Supported by the QO Service Wrap to ensure that the platform has 100% uptime and is updated regularly
Cyber Asset Attack Surface Management can be seen as just one highly important element of the much bigger picture of sustainable business asset management.
By contrast, addressing the asset management problem with Quod Orbis CCM will allow you to gain rapid visibility and control of your whole organisation’s assets. That’s because Quod Orbis CCM automates the creation and maintenance of a 100% complete and accurate asset inventory as one of its very first steps.
Moreover, CCM brings the all-encompassing and far-reaching benefits of continuous monitoring of all your assets and controls, so it’s a complete and sustainable solution.
Quod Orbis CCM allows you to achieve not only CAASM and business asset management but extends that visibility to monitor all your controls in real time through a single source of truth, while also providing expert operational support as well as board-level reporting.
How can a CAASM Solution manage a whole business inventory?
Our platform leverages automation to automatically scan your organisations infrastructure and with our low code, no code – once connected we can be delivering tangible, actionable intelligence to you within a matter of a few hours;
Full holistic coverage: traditional methods only tracked managed assets so other forms of legacy kit long forgotten or only tracked by standalone tools means so much can be left vulnerable. Our CAASM solution will use automation to discover, categorise and analyse any device, apps, or other tech and provide you a bespoke report (based on your requirements) so that you obtain a real-time accurate view of your threat landscape.
Assurance that you are viewing your business critical assets: The QO solution will work with you to ensure that you are receiving the viewpoint of your assets as you need to see them and so eliminating that manual static viewpoint that may not always be relevant to you.
Fully Customisable: Our experts are able to customise the platform to the threat levels you need to understand. No two businesses are the same so levels of threat will vary depending on your technology infrastructure. Our CAASM platform is agnostic in its approach and will encompass all your tech and place variables depending on your acceptable thresholds of risk.
What is the History of CAASM?
The emergence of vulnerability management really started in the 2000s after the growth of the internet and the proliferation of software applications; vulnerabilities in software code became a major concern. So the term vulnerability management gained traction when organisations started to focus on identifying and patching software vulnerabilities as part of their overall security strategy.
In the 2010’s Attack Surface Management developed as a comprehensive approach to identify all potential points of entry that an attacker could exploit but expanded beyond software vulnerabilities into exposed services, misconfigurations and potential points of compromise. At the same time automation and continuous monitoring was developed as the attack surface became more dynamic due to the cloud, IOT devices and mobile applications, meaning that traditional vulnerability assessments were no longer sufficient to adapt to the rapidly changing landscape. So continuous monitoring began to be developed to provide real-time insights into an organisations attack surface.
The integration of Attack Surface Management with threat intelligence became crucial around the same time. Organisations needed to understand the evolving threat landscape to prioritise their security efforts effectively. By combining information about potential vulnerabilities with threat intelligence data, companies could better anticipate potential attacks and take proactive measures to mitigate risks.
Today, Attack Surface Management continues to evolve as a critical aspect of cybersecurity. Organisations are embracing approaches that not only identify vulnerabilities but also assess the overall risk associated with their digital assets. This includes evaluating the impact of potential breaches and the likelihood of attacks occurring. Furthermore, the focus is shifting towards proactive measures, like security hygiene, reducing exposure and optimising configurations to minimise the attack surface.
Other CAASM Resources you may find useful
The Quod blog
Latest cyber security and risk insights, analysis and thought leadership delivered to your inbox
Fancy a chat about propelling your operational resilience?
Book a time that suits you to see our Continuous Controls Monitoring platform.