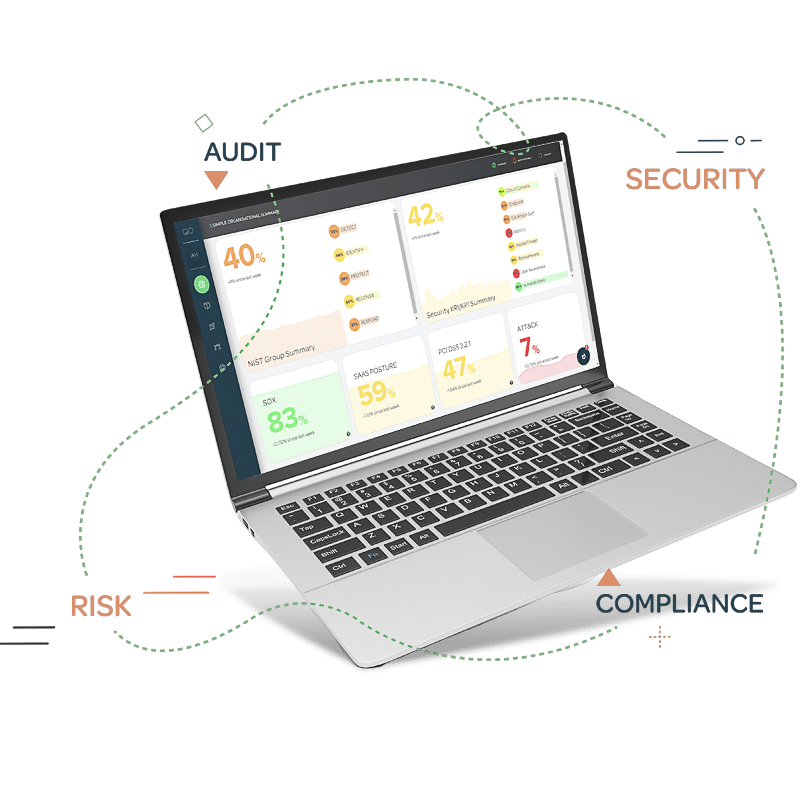
Navigating the CSPM Page

What is Cloud Security Posture Management?
Cloud Security Posture Management (CSPM) is a tool that is dedicated solely to the protection of an organisation’s assets and data in the cloud environment. CSPM has increased in importance as a result of organisations increasingly adopting cloud services, so the need to ensure that there are effective security measures in place has become increasingly imperative. Cloud Security posture management is such a solution that can identify, manage and mitigate security risks in the cloud infrastructure and applications.
Why is Cloud Security Posture Management Important?
Cloud Security Posture Management is imperative for businesses that operate in the cloud.
There is a misconception that removing your data and your organisations most valuable digital assets away from hardware servers that are vulnerable to cyber-attack will ultimately provide the security needed. However, businesses are often deceived by the implication of that action; moving all valuable assets into the cloud – is simply relocating your systems and data to servers in external buildings that are equally penetrable to attack.
Implementing CSPM is imperative to protecting data, mitigating and identifying risk and providing a holistic view of your cloud security posture. CSPM is the missing piece in the cloud environment, where a level of controls and metrics is as important as when managing internal assets. So the benefit of Cloud Security Posture Management is the consistency it provides in security meaning that overall governance is adhered to regardless of where the data exists.
What are the key benefits of Cloud Security Posture Management?

Vulnerabilities & Risk Assessment
Cloud Security Posture Management can analyse the entire cloud environment and identify potential security vulnerabilities and risks, including evaluation of encryption settings, network configuration and access controls.

Configuration Management:
Monitor and Assess tools review the configuration settings of cloud resources such as virtual machines, storage, databases and networking components. They ensure that these configurations adhere to security best practices and compliance standards.

Incident Response:
As a fully automated platform, CSPM can align to any controls and alert and facilitate a rapid response to any security incident or any deviation from a security policy. The platform will follow incident response procedures regardless of where the data is and alert via upstream ticketing.

Compliance Monitoring:
CSPM helps organisations adhere to regulatory requirements and industry standards by continuously monitoring cloud configurations and ensuring compliance with specific security policies.
Integration with DevOps:
CSPM tools often integrate with DevOps processes to ensure that security is considered throughout the development lifecycle. Integrating a cloud security posture with DevOps identifies and remediates security issues.
Customised Reporting:
Customised reports provide a complete holistic visibility of an organisations cloud security posture, ensuring security teams total assurance, allowing for prioritisation of remediation efforts.
Why do Businesses need to implement Cloud Security Posture Management?
With the exponential rise in the use of cloud services, organisations need to consider how they implement Cloud Security Posture Management; the key benefits of CSPM discussed above all contribute to the security of an organisations data. Ultimately, as data and applications are migrated to the cloud, many organisations may not consider the levels of security needed to keep it safe; this is imperative and crucial and Cloud Security Posture Management provides enablement to businesses identifying and mitigating security risk, thus reducing data breaches and unauthorised access.
Not only that but CSPM encourages vendor-agnostic security, meaning they can work across various cloud service providers. This is beneficial for businesses that use multiple cloud platforms, providing a consistent and centralised approach to security management, thus encouraging the protection of an organisations reputation and maintains customer trust.

How does CSPM work?
CSPM monitors your Cloud Environment
Cloud Security Posture Management typically scans your cloud environment and continuously monitors and assesses your security configuration in your cloud infrastructure to remediate and mitigate risk.
Creates a live asset repository
CSPM creates a live asset repository including any assets in the cloud such as virtual machines, storage, databases and networking components.
Supports Security Policies
CSPM supports an organisation’s security policies by assessing the current configurations of cloud resources and checking for compliance.
Assesses Risk
CSPM assesses risk through continuous monitoring of your entire cloud environment, reviewing access controls, encryption settings, network configurations and other factors that could pose a security threat.
Notifies relevant teams
If a security incident is identified CSPM will alert and notify the relevant security team(s) to ensure speedy remediation
reporting & Scaling
Customisable dashboards and reports.
CSPM is scalable and supports a multi cloud environment.
How does CSPM relate to Continuous Controls Monitoring?
CSPM specifically addresses the security posture of an organisation’s cloud infrastructure. It involves monitoring and managing security configurations and settings in cloud environments. Continuous Controls Monitoring in contrast is a broader platform that extends beyond the cloud and encompasses the continuous monitoring of controls and security measures across an entire organisation’s IT environment, which may include on-premises systems, networks, and cloud services.
CSPM is a subset of CCM, specifically tailored to address the unique challenges of securing cloud environments. Therefore, CSPM is an integral component of CCM for organisations that leverage cloud services.
How does our CCM Platform support CSPM?
Our Continuous Controls Monitoring platform continuously monitors cloud infrastructure configurations and activities in real-time, identifying and alerting teams of security misconfigurations, deviations from security policies, or any potential vulnerabilities in the cloud environment.
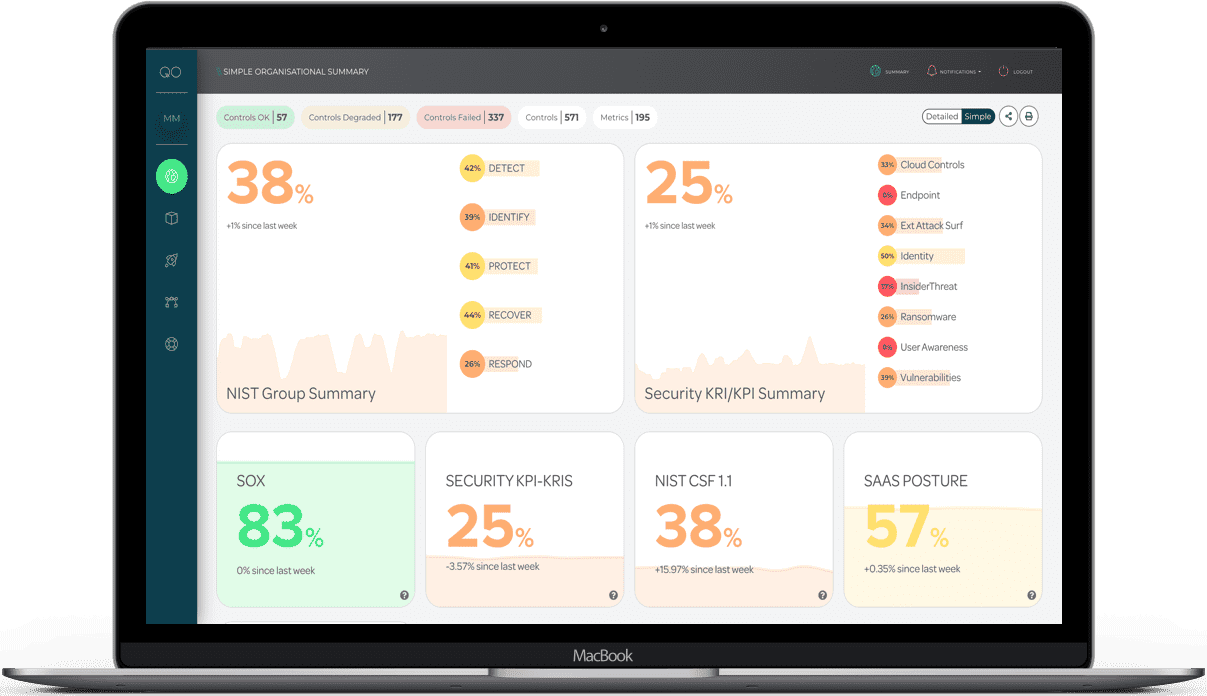
The platform is a comprehensive overview of your entire cloud environment, consolidating information from all your cloud environments into a unified view for total assurance of visibility across your entire cloud environment.
Access our Demo Platform
Explore the platform in your time
Contact one of our platform engineers to gain access now.
FAQ's
CSPM is compatible with all cloud platforms – AWS, Azure and Google Cloud for example.
Cloud Security Posture Management can operate across a multi-cloud environment and provides a unified view of an organisation’s security policies, so whether you are in one or multiple cloud environments, CSPM can monitor them all.
As with our entire Continuous Controls Monitoring platform, our CSPM can support any regulatory compliance framework and security standards your organisation needs to monitor, including internal and external frameworks.
CSPM scans continuously your entire cloud environment including detecting open ports, insecure network configurations, unencrypted data storage and other potential vulnerabilities. It monitors your security policies are correctly configured in your cloud environment and whether they are consistently applied; these policies cover areas such as identity and access management, encryption settings, network security and data storage. CSPM then assesses risk and alerts should it discover any and supports the remediation process applying corrective actions.
In short – YES! CSPM monitors continuously and alerts the appropriate teams if necessary, even creating upstream ticketing for issues to be resolved, significantly reducing the manual effort needed.
Our platform connects to any data source and any technology, aligning to any framework. This seems like a bold statement, but the way in which our technology is built allows no API to be a challenge and DevOps pipelines are no bother.
Customised reporting and analytics are essential for each business. Our team build the dashboards you want from operational to board level. You tell us what you need, we will build it!
Scalability is no issue for our CSPM solution within our platform. We just need to connect and, should you add more cloud environments in, that is no bother as our CSPM is by design capable of scaling however your organisation needs.
CSPM is a component of CCM. If your organisation is solely in the cloud then yes! Our platform can facilitate your requirements for a cloud-only environment. CCM monitors an organisations entire IT environment – so it is a larger and broader capability. CSPM is a subset of CCM.
The Quod blog
Latest cyber security and risk insights, analysis and thought leadership delivered to your inbox
Get in touch
Contact us today for more information on our cyber and risk consultancy services, or for an initial chat about your needs or concerns.