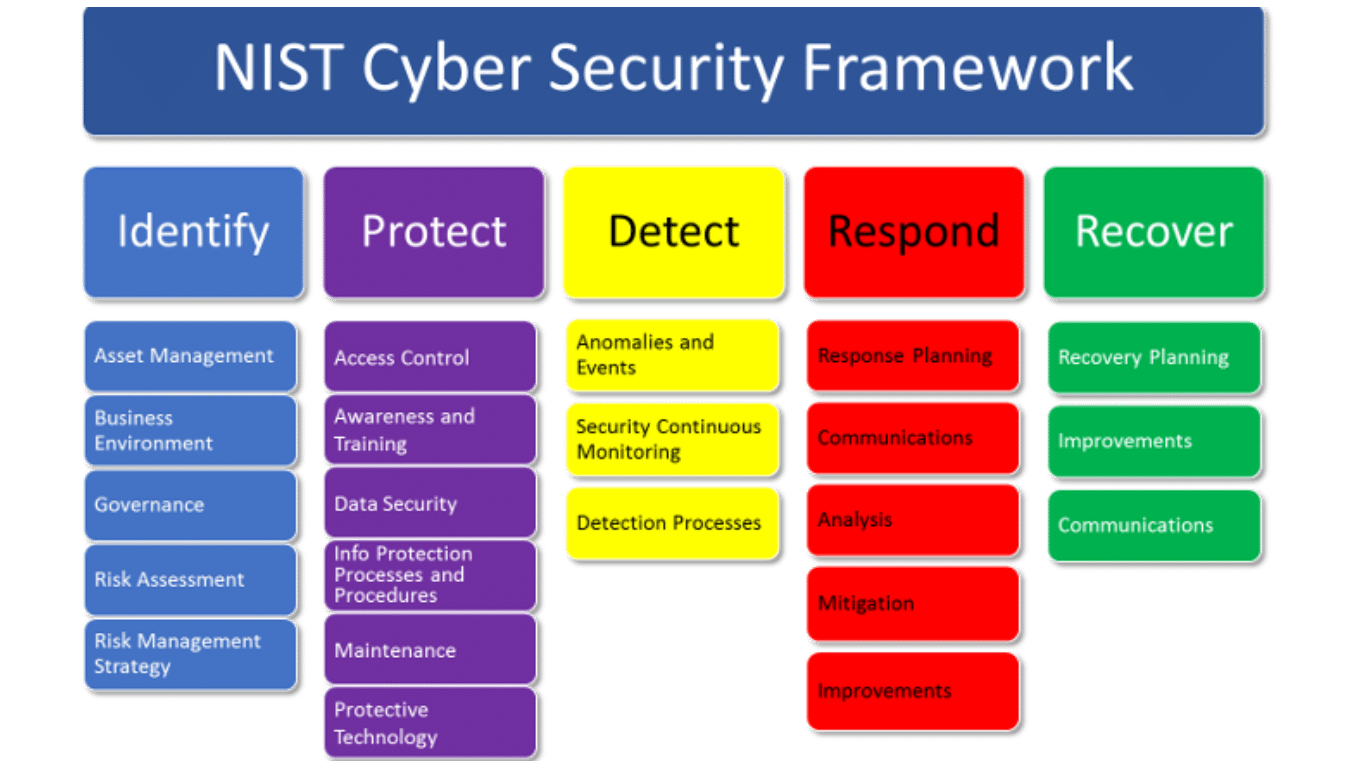
NIST Cyber Security framework is widely recognised and adhered to by most enterprise organisations, focusing on guidelines and best practises for improving cyber security. The guidance it provides is invaluable to organisations, however it poses many challenges in maintaining complete regulatory compliance.
Adherence can be challenging for a number of reasons:
Complexity: Comprehensive and detailed, the NIST framework can be overwhelming for any organisations or those with limited or stretched cyber security resources. There are multiple components to the framework as well as subcategories and reference documents, making it difficult to implement comprehensively.
Resource Intensive: The simple fact is that you need a significant investment of time, money and skilled teams in order for any organisation to adhere to NIST. Many businesses may struggle to allocate such resources in order to fully implement the necessary requirements.
Lack of Standardisation: A huge challenge is that NIST is not prescriptive. It provides a framework, but there is currently a lack of standardisation so organisations have to interpret and adapt to their specific needs and risk profiles. This lack of standardisation therefore makes it difficult for organisations to determine which controls and practises are relevant for them.
Evolving Threat Landscape: The cyber security threat landscape is constantly evolving, with new threats and attack vectors emerging regularly. Adhering to the NIST framework requires organisations to stay up to date with these changes and adapt their security measures accordingly. This can be challenging if the resource and monitoring capabilities are not present.
Organisational Resistance: Implementing the NIST framework often involves changes to organisational culture, policies and practices. Resistance to change within the organisation can be a significant challenge.
Cost Considerations: Many of the security measures recommended by NIST can be expensive to implement and maintain so enterprises need to be fully appraised of the cost to adhere to the regulation.
Integration Challenges: With most enterprises, there are already existing policies, systems and technologies, so to Integrate NIST’s guidelines into these can be exceedingly complex. In particular businesses that have an abundance of legacy technology may not have the necessary security measures in place to be able to support the NIST framework which will require extensive planning and investment.
Skill Shortage: Cyber security expertise is in high demand and organisations may struggle to find and retain skilled personnel who can effectively implement and manage security measures in line with the NIST framework.
Continuous Monitoring and Improvement: NIST emphasises the need for continuous monitoring and improvement of cyber security practices. This can be a challenge for organisations that lack the necessary tools (such as CCM) and processes to continually assess and enhance their security posture.
How can Continuous Controls Monitoring support an Organisation’s NIST Regulatory Compliance?
NIST is a valuable framework for improving cyber security and is a long-term commitment rather than a one-off task.
Continuous Controls Monitoring (CCM) is a crucial component of an organisation’s risk management and compliance strategy. When integrated with the NIST framework, CCM can help ensure that an organisation’s information security and compliance efforts are effective, efficient and aligned with best practices; particularly Continuous Controls Monitoring supports NIST compliance by:
Asset Management: CCM can support NIST’s recommendations for effective asset management by helping organisations maintain an up-to-date inventory of assets, including hardware, software and data. In fact, this capability in CCM means you can be compliant with the first guideline of every framework.
Identifying and Prioritising Controls: CCM helps organisations identify and prioritise security controls based on their criticality. It continuously monitors these controls and alerts on any deviations or non-compliance, allowing organisations to focus their efforts on areas where they are most needed.
Automated Monitoring: CCM automates the monitoring of security controls, ensuring that they are consistently applied. This aligns with Nists focus on automation to improve security and compliance.
Real-Time Visibility: CCM provides real-time visibility into an organisation’s security posture. This helps in the early detection of security incidents or compliance violations, allowing for prompt response as recommended by the NIST Incident Response framework.
Data Integrity and Accuracy: CCM systems ensure the integrity and accuracy of the data used for monitoring controls. Accurate data is essential for risk assessment, as per NIST’s guidance on risk management.
Risk Assessment: CCM tools can help organisations assess and quantify risks based on the continuous monitoring data. This aligns with NIST’s risk management framework which is a fundamental component of the NIST Cyber Security Framework.
Compliance Mapping: CCM tools can map monitoring capabilities to specific NIST controls, ensuring that an organisation is compliant with NIST’s cyber security standards.
Customised Reporting: CCM tools generate reports that provide evidence of compliance, making it easier for organisations to demonstrate adherence to NIST guidelines during audits and assessments.
Response and Recovery: In the event of a security incident CCM data can be crucial in helping organisations respond and recover in line with NIST’s guidelines for incident response.
Continuous Improvement: CCM allows organisations to continuously measure and improve their security and compliance posture which is in line with NIST’s framework for continuous improvement and adaptability.
Essentially, Continuous Controls Monitoring supports the NIST framework by automating asset management, effectiveness of controls, improving risk management, facilitating compliance and ultimately providing the real-time visibility that organisation’s need to comply with NIST. By harnessing the power of CCM, organisations can maintain a strong security posture and be effective in their regulatory compliance.